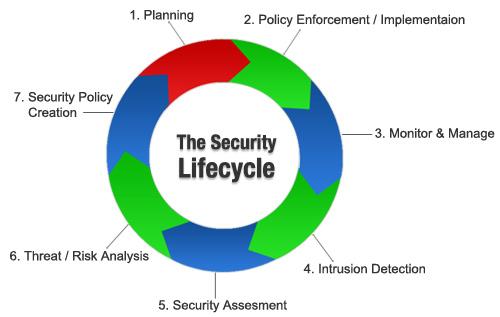
Regardless of the elapsed time of a security breach, the fact is that one day is far too long, and by the time a breach is detected. Data is often compromised during the initial breach. Organizations need a more intelligent approach to detect threats earlier and turn the tide against sophisticated cyberattacks.
Subscribe To Our Newsletter
Join our newsletter to get the latest blogs, updates and special offers delivered directly in your inbox.